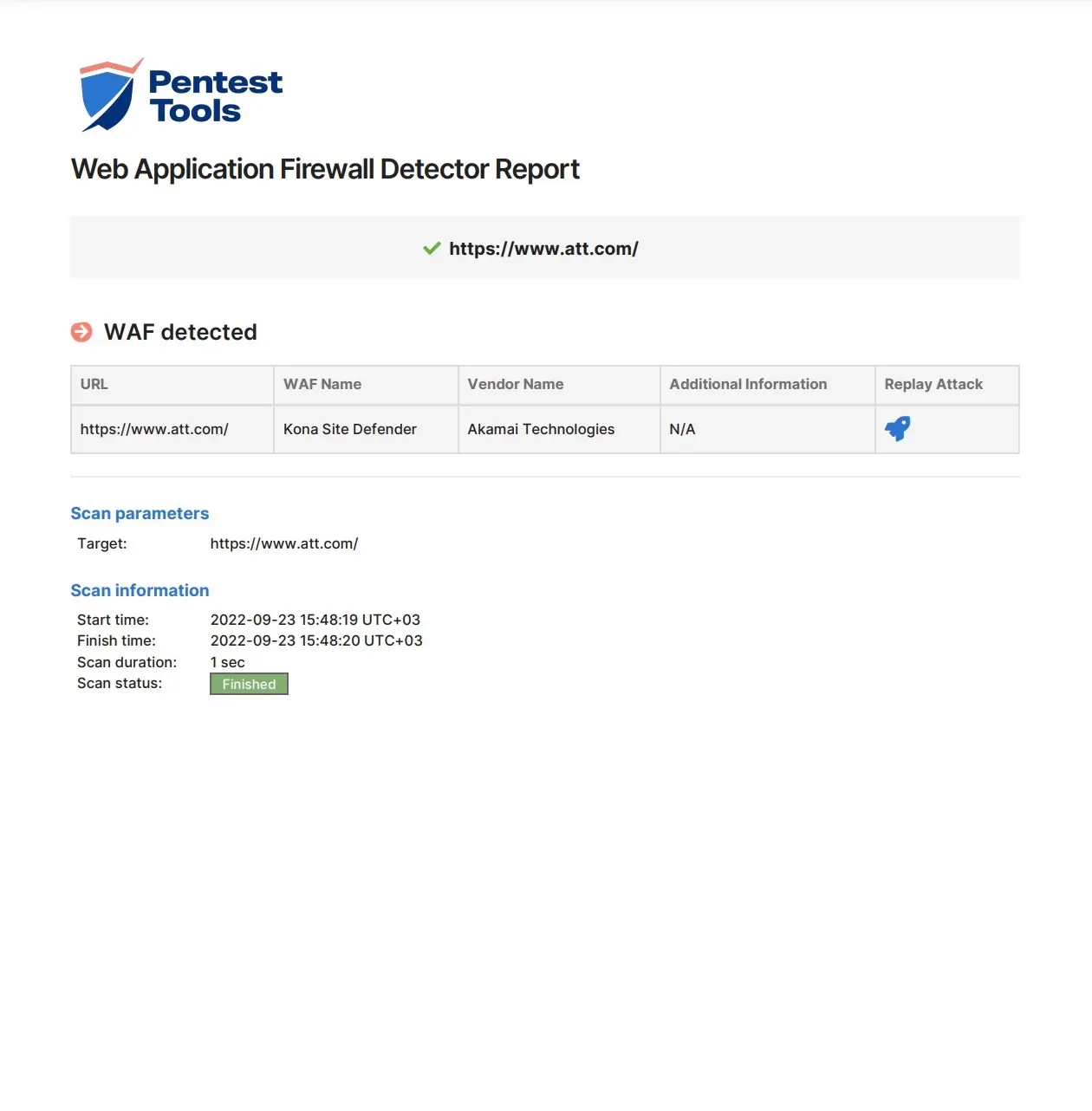
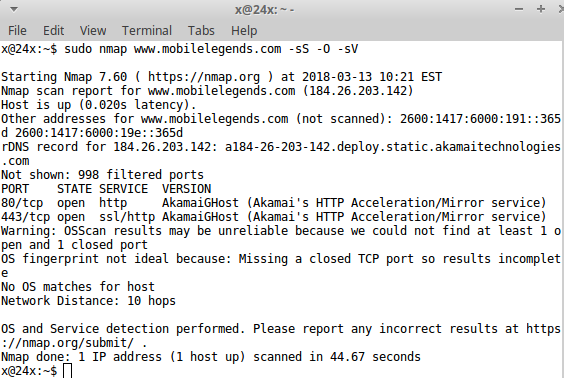
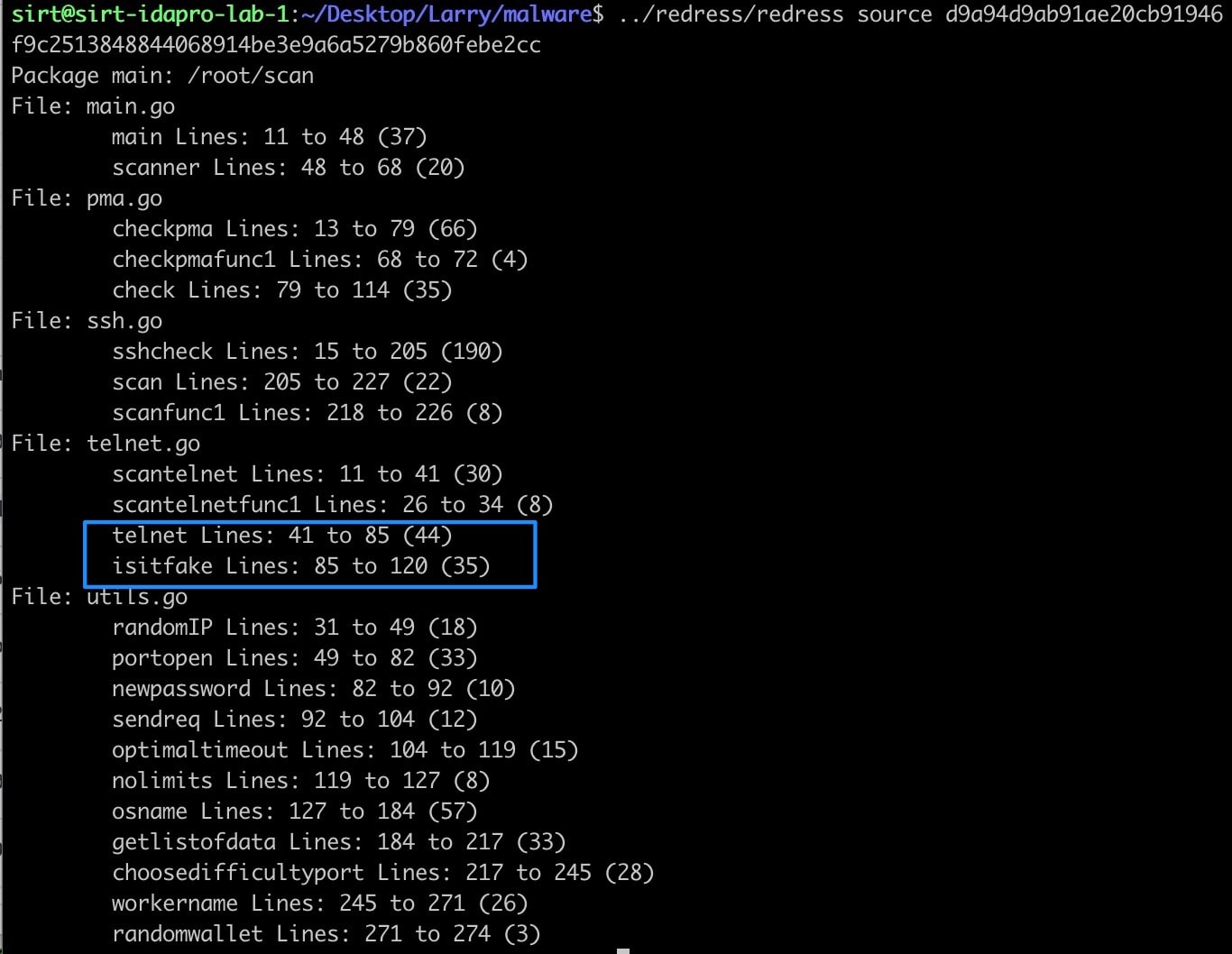
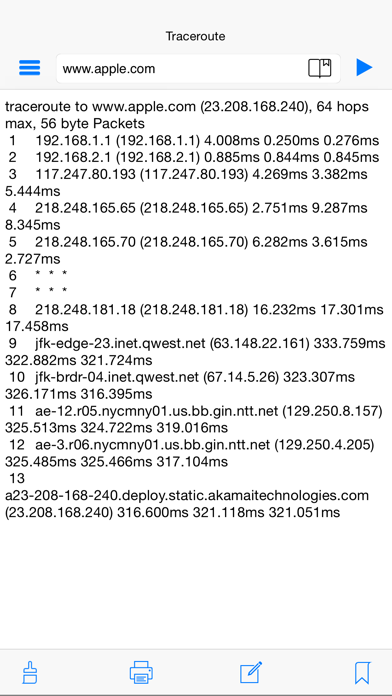
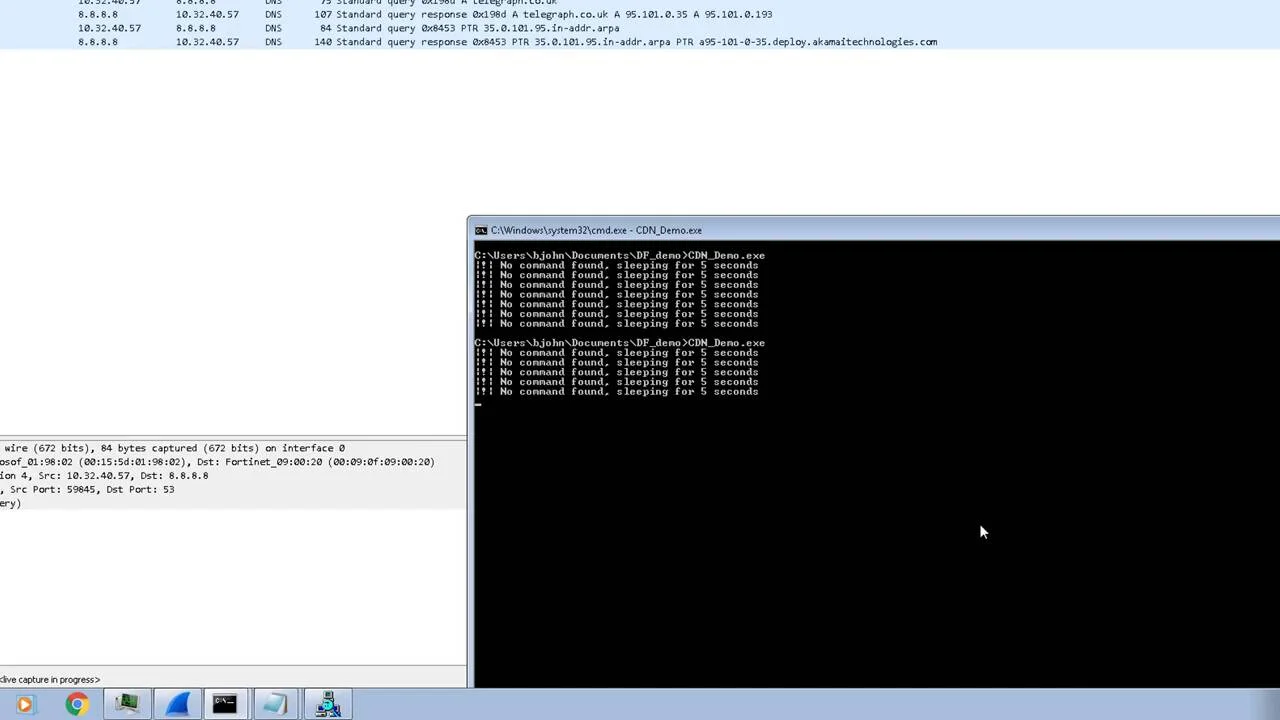
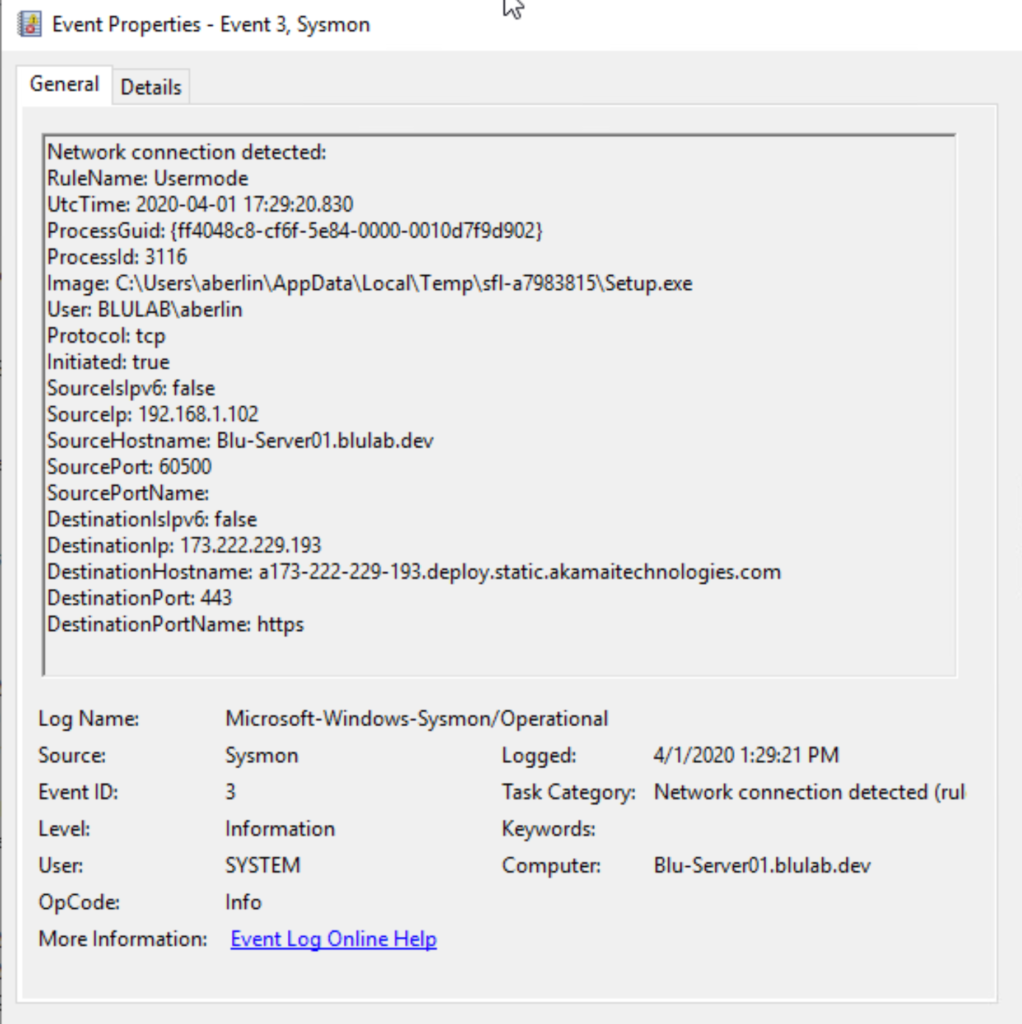
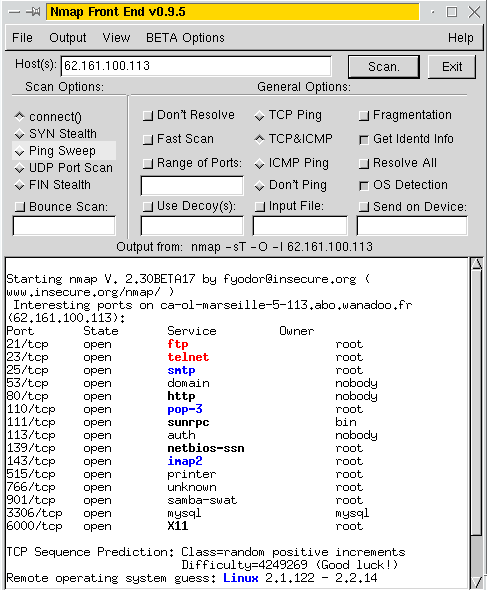
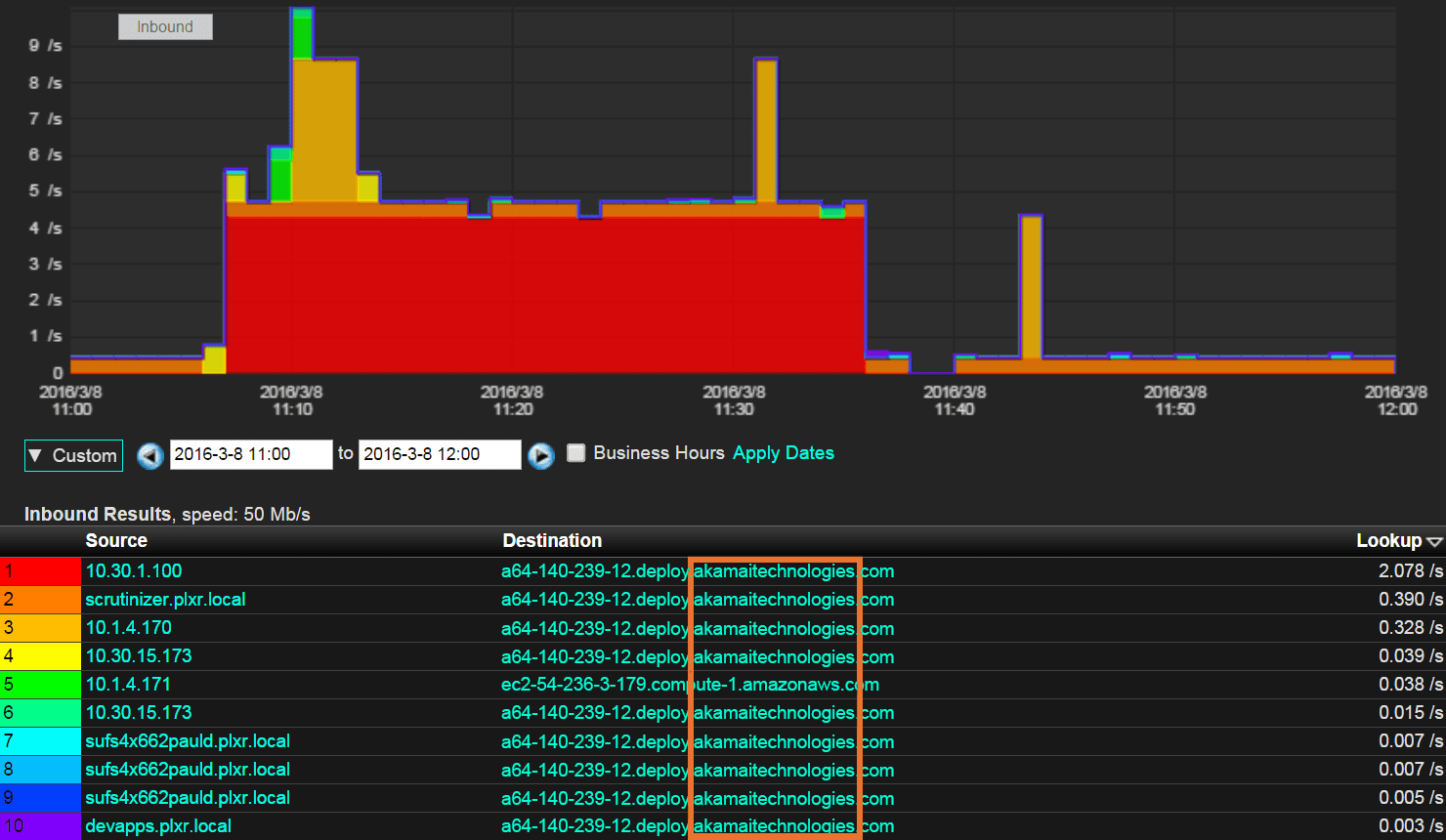
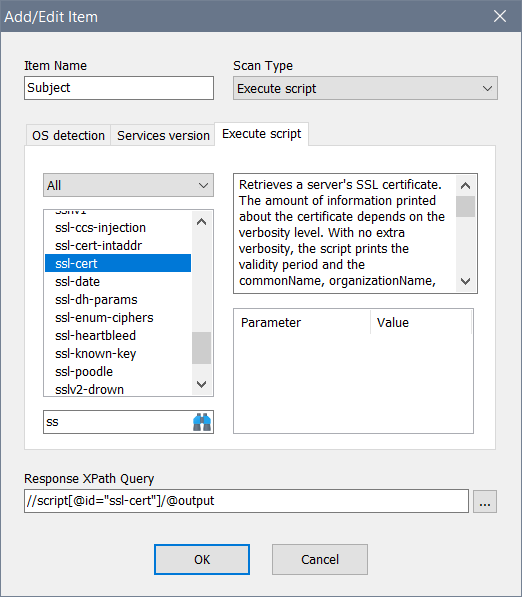
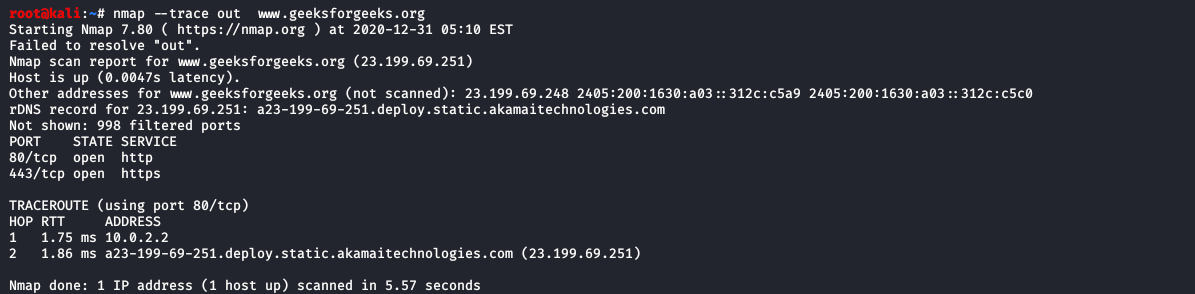
Evasion Tactics For Scanning Targets (Active Scan) | secybr | penetration testing, red teaming and hack tricks.

Evasion Tactics For Scanning Targets (Active Scan) | secybr | penetration testing, red teaming and hack tricks.
Automated Malware Analysis Report for http://a2-22-69-126.deploy.static. akamaitechnologies.com - Generated by Joe Sandbox